360 Degree Cybersecurity
Software Application Security
Overview
The rapid evolution of cyber threats can be destructive for the business you created with love, care and utter hard work. At Intigate, we use cutting-edge technological solutions to build customized security programs aimed at reducing cyber risk. With our 360-degree cybersecurity services, you can ensure privacy, client trust, as well as financial and operational integrity of your growing business.
Our 360 Degree Cybersecurity Capabilities
Our 360˚ cybersecurity solutions are tailored to improve the safety of your IT systems, making them more reliable and safe for storing and exchanging sensitive business information.
Cloud-Based Data Protection
We provide cloud optimization services aimed to improve data protection, backup, and host mission-critical applications—all while lowering cyber risk.
Advanced Scalability
Our versatile technological and cybersecurity solutions can adapt to your changing business needs.
Data-Driven Approach
We provide detailed insights by analyzing real-time data to improve business functions’ visibility and help with effective and quick decision making.
Threat detection through AI& Machine Learning
Our top-notch AI services automate time-consuming administrative tasks and get valuable insights through data analysis and helps security operations stay ahead of threats.
Value-Driven Tech Investments
Our thoughtful technological implementations not only provide high returns on investment by boosting your organization’s productivity and efficiency but also secure your organization multi-dimensionally.
Internet of Things (IoT) to Rescue
We have developed the capability of harnessing the power of IoT for transferring and securing data quicker and more efficiently according to industry-specific requirements.
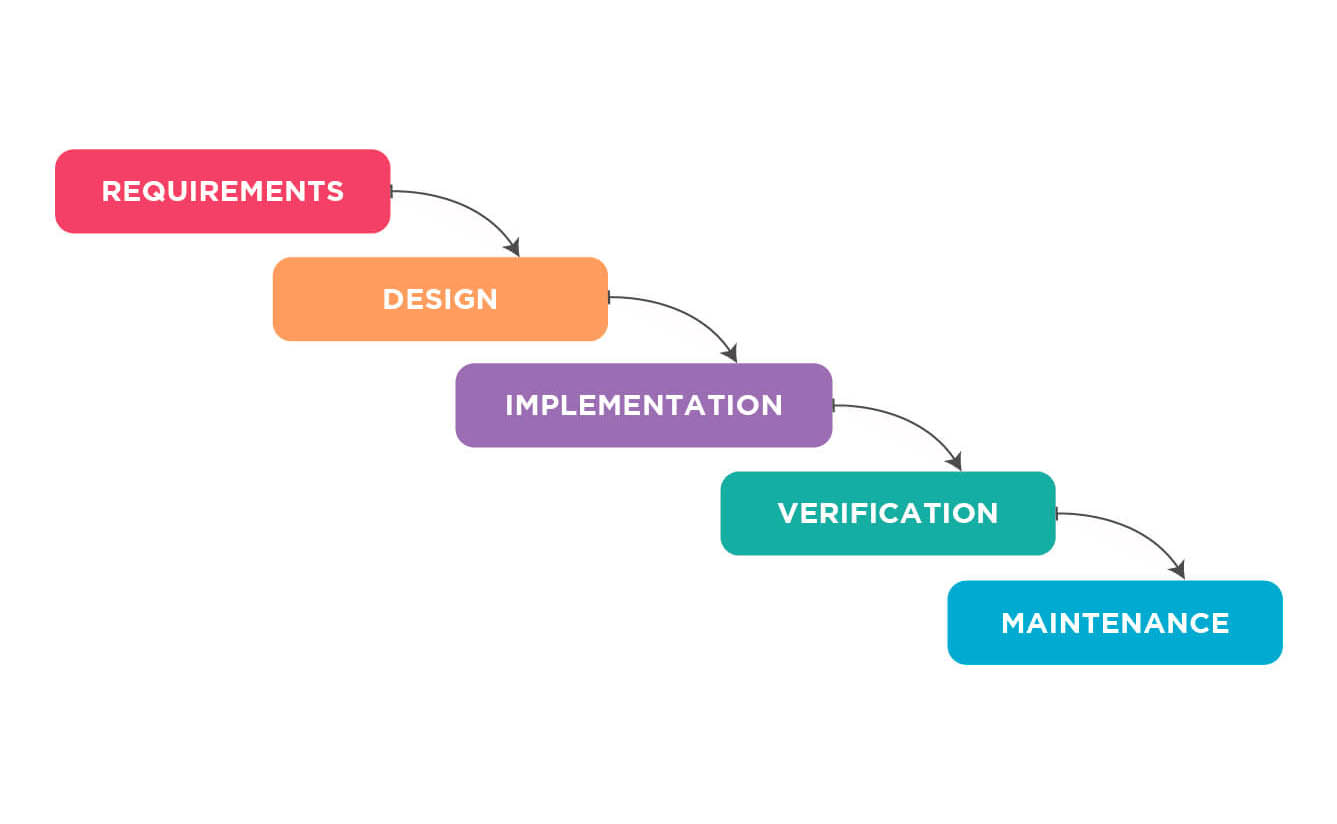
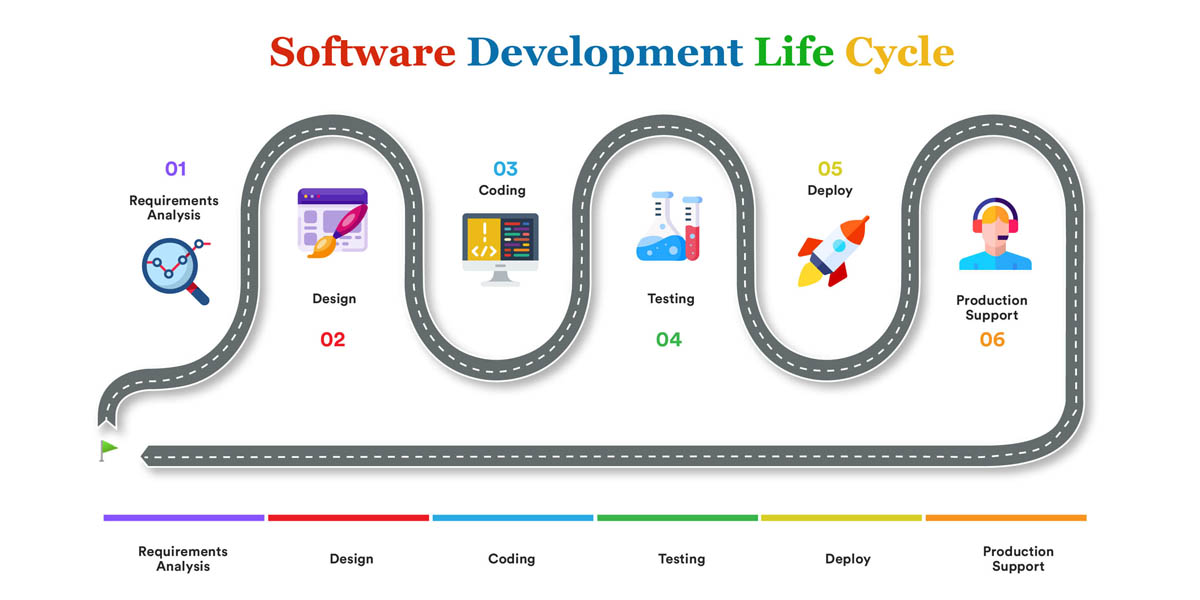
SDLC Process – 360 Degree Cybersecurity
We provide end-to-end software product development and specialized technological services to meet your specific business needs. When our clients involve us right from the onset of production conceptualization, we build robust solutions that are scalable and user-friendly.
We begin by collecting relevant information as per your request and requirements from the project.
We develop high and low-level software architecture and UI screens using the information obtained previously.
Using agile methodologies, we divide project modules and begin coding the system using suitable programming languages and coding guidelines.
Our QA testing team tests the functionality of the code to identify and fix bugs that improve the solution’s performance.
Our team deploys the finalized version of the software or application to it can be launched to target your user market.
As per your SLA, Intigate ensures that ongoing needs for maintenance and support for the deployed solution are met effectively.
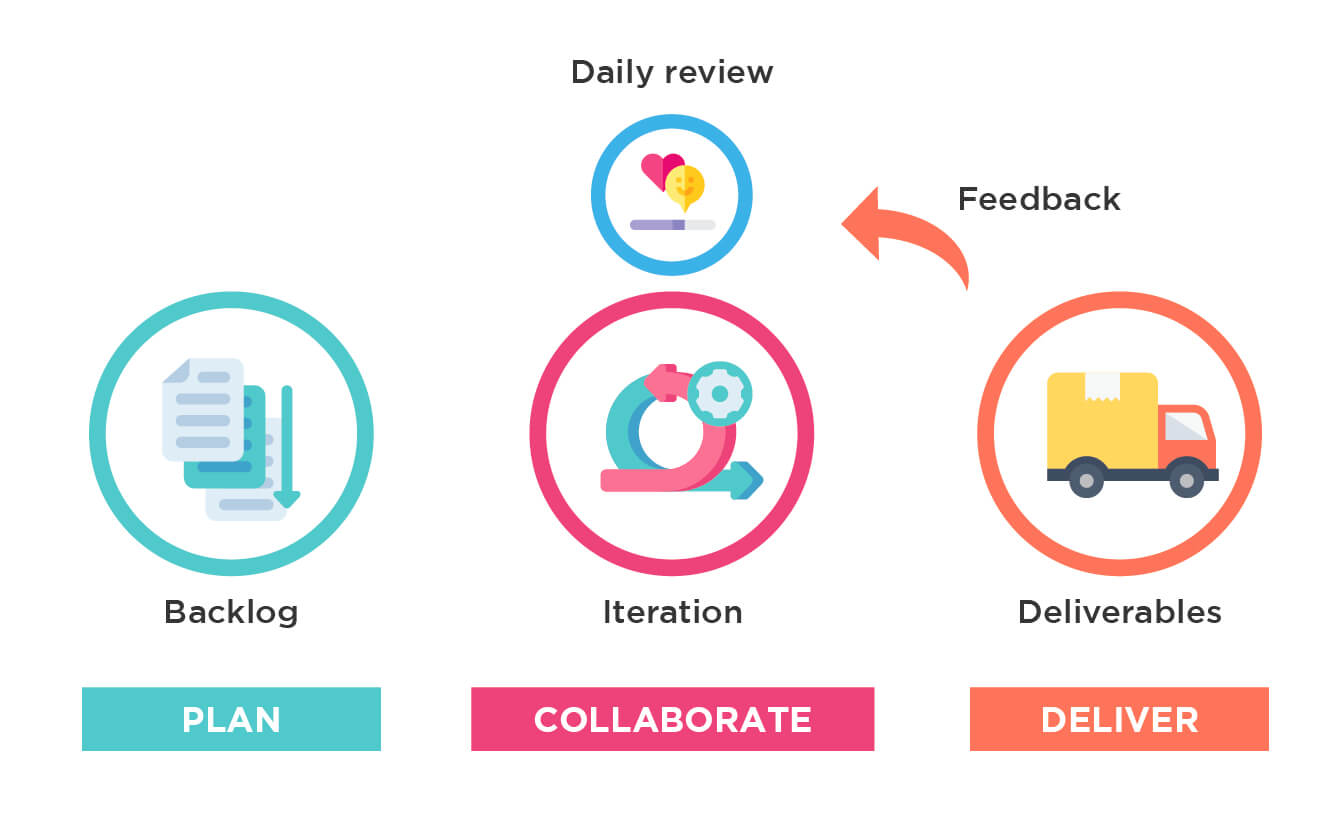
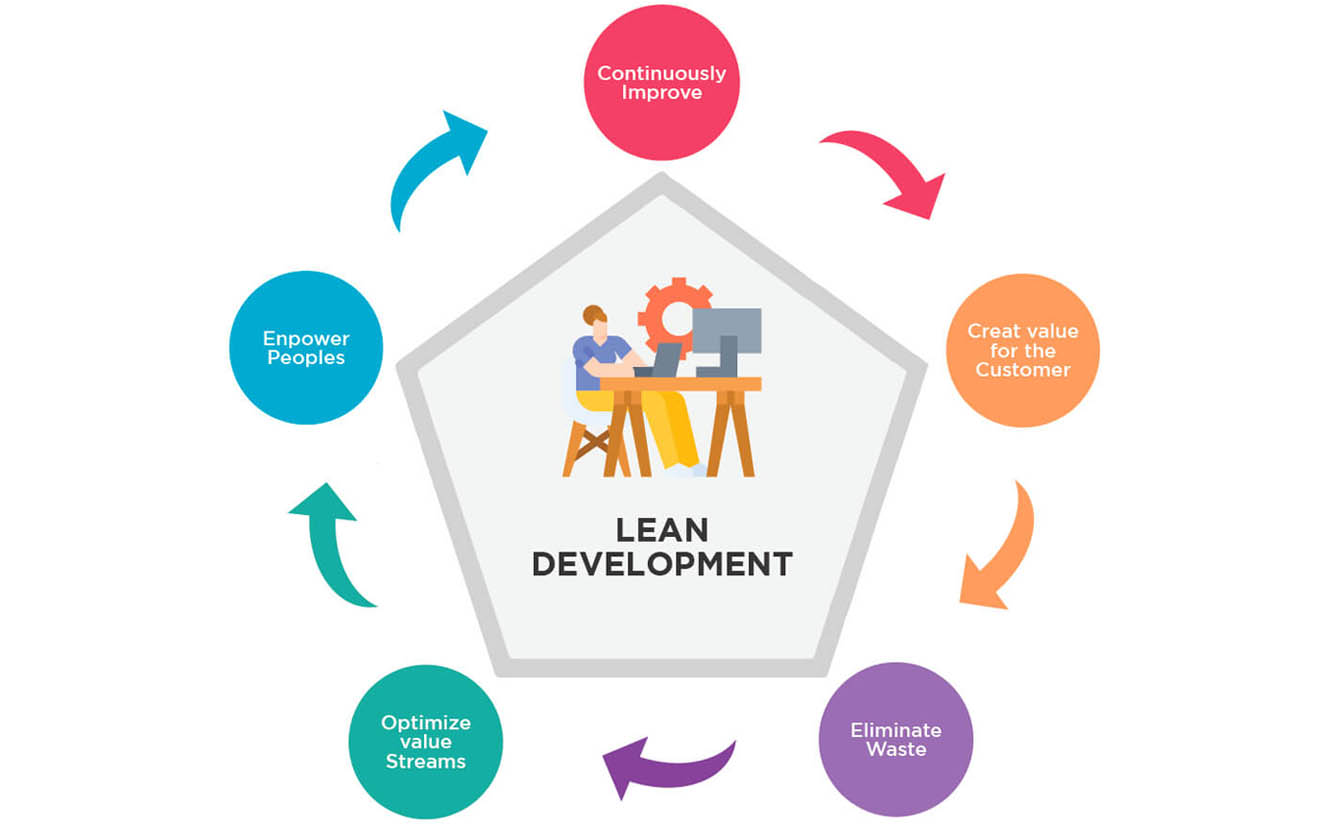
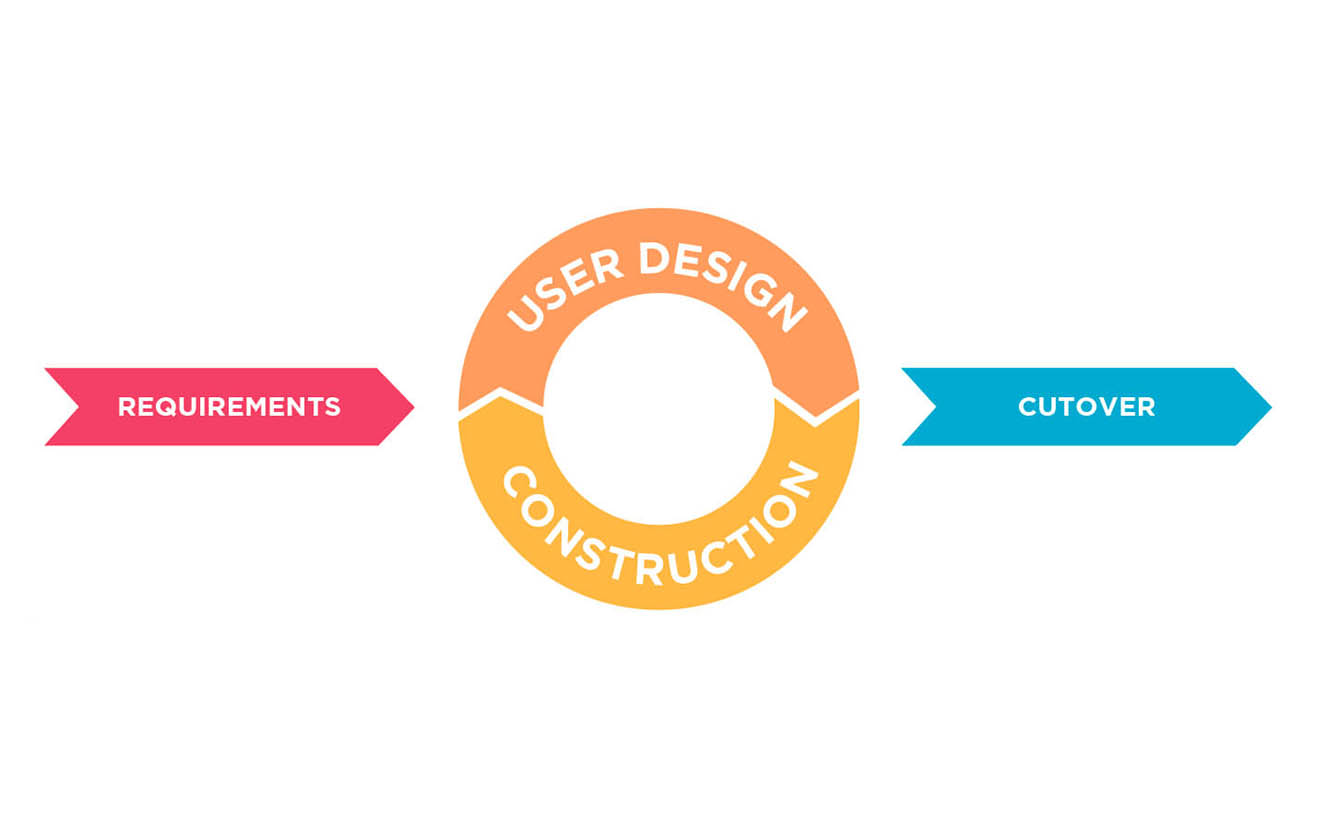
Our Approach
While designing software product development solutions for our clients, we move away from the one-size-fits-all approach and work with you to analyze, build and deploy a final product that can boost innovation and productivity. Our most popular development/operational models include:
Full-Stack Technologies & Tools We Champion
We Have Competencies in a Wide Range of Technologies
Back end
Front end
Mobile
Desktop
Databases / data storages
Cloud databases (DBaaS)